Cybersecurity Monitoring - Its Work, Steps, Tools & Strategies, Business.
19th July 2024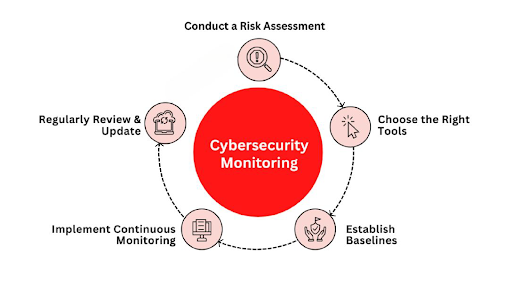
Understanding Cybersecurity Monitoring- A Key To Safe Networks
Cybersecurity monitoring is a proactive measure, constantly keeping an eye on system activity and network traffic to detect and respond to security incidents. It's about being prepared and in control, helping catch and deal with security issues quickly. Unlike traditional methods that try to stop attacks before they happen, cybersecurity monitoring focuses on detecting and handling threats that slip through.
On the other hand, prevention is essential; sometimes, it is impossible to prevent all the attacks. That's where Cybersecurity monitoring steps in to find and fix the issues after they have broken through. Continuous cybersecurity monitoring is a crucial part of any organization's security plan.
By constantly checking for and dealing with potential security problems, organizations like HarpyCyber can protect their data and minimize the impact of breaches and other cybersecurity risks.
How does Cybersecurity monitoring work?
Cybersecurity monitoring involves monitoring network traffic and individual devices using various tools and strategies.
Network monitoring refers to checking traffic flow to detect suspicious activity, such as unexpected data transfers or multiple login attempts from unknown devices. When chances increase that something is wrong, this will find weak spots in the network and send real-time alerts.
Moreover, Endpoint monitoring helps focus on individual devices, such as laptops and smartphones, to detect suspicious behavior. This will look for doubtful activity to detect threats like malware and ransomware that might slip past network defenses.
By constantly watching for cyber threats, businesses can quickly respond to incidents, boost their Cybersecurity that comes across with regulations, and reduce security issues.
Let's break it down in steps to explain briefly: Collection of Data: Cybersecurity monitoring starts with collecting data from various sources like servers, network devices, and endpoints. This data involves network activity logs, security alerts, system logs, and other doubtful information that can be used to identify future threats.
Data Interpretation: After collecting the data from sources, it is analyzed using different techniques, including statistical analysis, behavioral analysis, and machine learning. The primary purpose of this process is to identify any suspicious activity that could indicate a severe & future threat.
Detecting Threat:After getting results, if unusual threats are detected, the cybersecurity monitoring system will initiate alerts and send them to the systems via email, SMS, or the monitoring platform itself.
Response & Mitigation:Cybersecurity monitoring will guide handling incoming threats, such as blocking network traffic or isolating an infected device. The security team can then look at the alert and decide if more actions are needed, like a full investigation, or if only fixing the issue will be enough.
Continuous monitoring of the systems is not just a practice, it's a necessity:Cybersecurity monitoring is an ongoing process. The system will always check and analyze the data from various sources to spot future threats. This urgency helps businesses respond quickly and effectively, reducing the damage a future attack can cause.
Step 1: Conduct a Risk Assessment Start by discovering what needs to be protecting the threats it faces and any weak spots in your network. A risk assessment helps you understand your organization's dangers and alerts you to prioritize security efforts. Always look at your network traffic, spot weak points, and think about the impact of a data break.
Step 2: Choose the Right Tools
Empower your security efforts by choosing the right tools that align with your business needs. These tools should provide:
- Real-time alerts and analysis.
- Perfect detection and response to security incidents.
- The ability to identify threats and analyze network traffic to spot suspicious activity before it causes damage.
Step 3: Establish Baselines Establishing baselines for regular network activity is crucial for detecting future security incidents. You can spot anything unusual quickly by understanding regular network activity. This step will help you analyze traffic patterns and typical user behavior and set up alerts for deviations.
Step 4: Implement Continuous Monitoring Monitor your network traffic and system activity to find and respond to security incidents in real-time. This includes detecting threats that respond to incidents and analyzing severe traffic issues.
Step 5: Regularly Review & Update Regularly review and update your cybersecurity strategy to maintain security and control. Assess the effectiveness of your current measures, identify areas for improvement, and make necessary changes. By staying attentive and updating your strategy, you can minimize downtime, prevent data breaches, and keep your organization secure. Now, let's talk about the tools and strategies that make these monitoring strategies effective.
Step 5: Regularly Review & Update Regularly review and update your cybersecurity strategy to maintain security and control. Assess the effectiveness of your current measures, identify areas for improvement, and make necessary changes. By staying attentive and updating your strategy, you can minimize downtime, prevent data breaches, and keep your organization secure. Now, let's talk about the tools and strategies that make these monitoring strategies effective.
Top Tools & Strategies for Effective Cybersecurity Monitoring
Security Information and Event Management (SIEM) Security Information and Event Management (SIEM) tools are the most powerful solutions to help you collect and connect security data from different sources, including network devices, applications, and servers. These tools use advanced algorithms and machine learning to get timely security alerts. This will help security teams identify and respond quickly to potential threats. SIEM tools can also generate reports and dashboards to provide insights into security trends and compliance status.
Intrusion Detection Systems (IDS) Intrusion Detection Systems (IDS) are versatile tools designed to monitor network traffic for signs of unauthorized access. These tools can detect various malicious activities, including malware infections, network scans, and brute force attacks. IDS tools can be deployed as network-based or host-based solutions depending on the organization's needs. They also generate alerts and reports that assist security teams in investigating and responding to security incidents.
Threat Intelligence Threat intelligence tools are used to gather and analyze data on future threats. This helps to identify and respond to newly created threats. It can come from open-source feeds, commercial risk intelligence providers, and internal security data. It helps security teams understand attackers' tactics, techniques, and procedures (TTPs). By leveraging these tools and strategies in unison, businesses can maintain constant vigilance over their networks and endpoints, swiftly detect and respond to security incidents, and fortify their overall security. This collaborative approach ensures a comprehensive security posture that is proactive and adaptive to emerging threats.
Why should every business run cybersecurity monitoring? Cybersecurity monitoring involves the continuous surveillance of your networks and systems for any signs of a potential cyber attack. This proactive approach is beneficial for all types of businesses, as it allows for the early detection and response to security threats.
1. Cybersecurity monitoring plays a crucial role in securing sensitive data, such as customer information, financial data, trade secrets, etc. By detecting and responding to potential threats, it provides a sense of security and reassurance.
2. Many industries, such as healthcare and businesses that handle credit card payments, have stringent regulations for protecting sensitive data. Cybersecurity monitoring plays a crucial role in ensuring compliance with these rules, such as HIPAA for healthcare and PCI DSS for businesses that accept credit card payments, thereby helping to avoid costly fines.
3. Data breaches lead to financial losses and a loss of customer trust, which can significantly damage your business's reputation. Cybersecurity monitoring plays a crucial role in maintaining this trust by helping you spot and stop breaches before they occur, thereby reducing the risk to your business and reputation. Doing this lets you detect future threats quickly and respond faster to save your data efficiently and effectively.
4. With the continuous increase in cyber attacks, businesses must stay ahead of the latest threats. Cybersecurity monitoring lets you be proactive, providing real-time alerts about potential threats. You can take immediate measures to protect your business by managing data logs and running analytics.
Other ways: 1. Keep software and operating systems up to date with the latest security patches and updates. 2. Implement strong passwords and two-factor authentication to help protect against password-based attacks. 3. Regularly backup important data to prevent data loss in a cyberattack. 4. Educate employees about safe internet practices involving phishing scams and suspicious email attachments.
How can Harpy Cyber help you enhance Cybersecurity Monitoring? In conclusion, we want to introduce you to Harpy Cyber, which specializes in establishing secure and robust cybersecurity solutions for organizations. They provide a range of proactive cybersecurity monitoring tools and services to improve an organization's network visibility and security posture. With the right tools, your businesses can be prepared and protected from the growing cyber-attack threats.
Contact Harpy Cyber now because even your grandma's cookie recipes deserve top-notch Cybersecurity!
