Steps to prevent and avoid becoming victim of phishing attack
25 July 2023
Phishing is one of the means hackers use to extract sensitive data. They present themselves as employees of renowned companies and manipulate the victims to disclose their information. It could be credit card numbers or login credentials too. The hackers use attractive offers to trick users into revealing personal data, leading to data misuse such as identity theft, fraudulent transactions, or other unauthorized account access. However, there is no need to panic, as you can protect your resources by being aware of scam messages, checking sources and hints of deceit using legitimate channels, regularly maintaining software updates, and looking out for telltale indicators. Here is the detailed guide for the phishing attack prevention checklist for 2023.
What is the checklist for preventing phishing attacks?
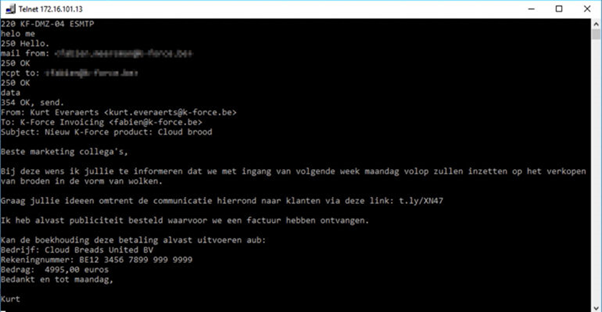
Cybercriminals or hackers use phishing to extract confidential information by impersonating a trustworthy entity via emails, text messages, or even unauthentic websites that present themselves as a reputed company, government company, or financial institute to get debit cards or credit card numbers with CVV that seems straightforward, yet they get desired results. Despite the introduction of fortified firewalls and a much-improvised defense, like a one-time password for your mobile phone, they successfully trick the individuals into clicking the links too good to be true. Phishing attacks come in many variations, like bait, hook, catch, and exploit, that deliver malware for taking funds to their bank accounts by pilfering individuals’ credentials. Below is the checklist to defend your data from phishing attacks.
Check the sender’s email address and implement adequate security: When you receive an email, it will help if you check for the sender's email address. You find a slight change or a spelling mistake in those emails with an authentic domain name in a phishing email. Use caution for the email domain you suspect or are unfamiliar with.
Check whether the email contains generic greetings: The difference between genuine business emails and phishing emails is that the former uses your name with personalized communications. On the other hand, phishing emails only mention “Dear User” or “Dear Customer.”
Make a thorough check for spelling and grammatical errors: An authentic email uses professional language devoid of spelling and grammar mistakes. If you don’t find these in your email, treat that as phishing.
Look out for threatening words: Phishing emails also generate threatening emails of hurrying up things and making you lose your mental balance to get the desired response. Such messages include a threat of closing your account, allegations of fraud, or issuing a grave warning like legal notice when you don’t respond. Hence, it will help if you become aware of such tricks.
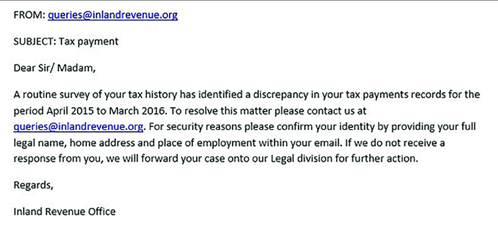
Please view the link without clicking: A mere hovering over the links gives you an idea of whether it is an authentic or phishing link. The content of a phishing email misdirects you to the wrong target. A legitimate website directs you to the company’s website.
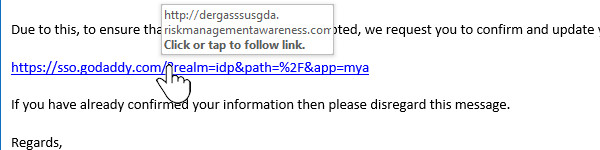
Be alert over the request for personal information: A reputed company never requests an individual for personal information. Hence, you must be aware of the email with CVV that asks for personal details like passwords, social security, and credit card numbers.
Thoroughly check email format and logos: An authentic email has an excellent layout and original logos. On the other hand, a phishing email has an equally poor email format, such as mismatched typefaces and distorted logos, including graphics of pathetic quality.

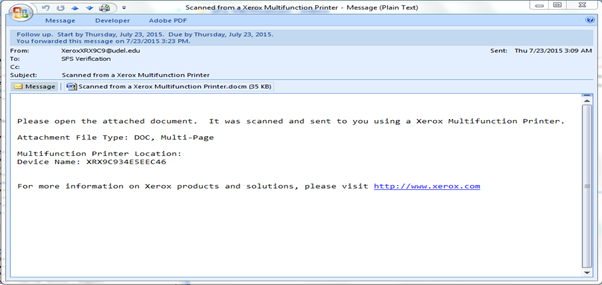
Avoid unexpected attachments: Even a phishing email can have attachments that contain viruses or malware. If you suspect a random attachment from suspicious sources, put it in the trash.
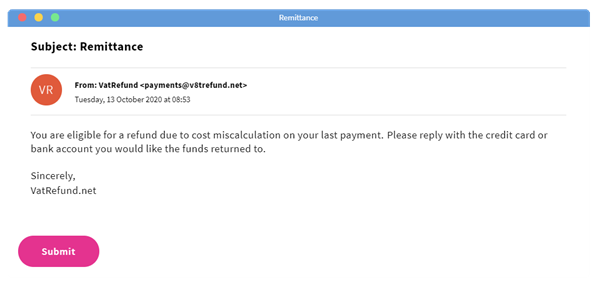
Verify them with the help of official channels: If you doubt the email, it will help if you contact the company via the official website to check the email's credibility.
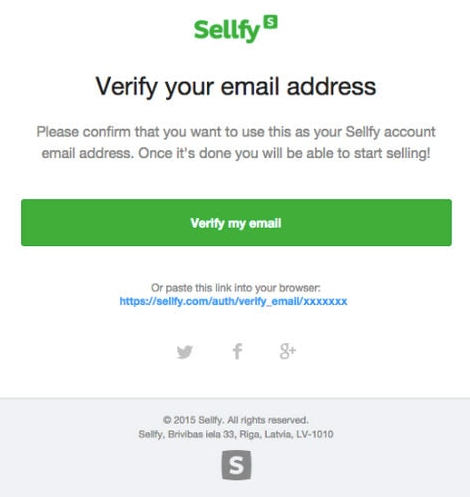
Believe in your intrusions: Some emails seem very attractive and too promising for you to believe. If you find anything fishy, it will help if you send it to the trash and report it to the concerned authority about that email. Your intrusions will never mislead you.
Conclusion:
As and when new threats emerge, the work of developing corresponding software also increases. It will help if you keep yourself updated on new threats. However, it would be best if you were always on your toes as the hackers come with different schemes for extracting sensitive data.
