Today’s cyber security challenges are complicated. And they rarely fit into the categories defined to run your business. Disconnected point products and services don’t provide the comprehensive solutions you need, when you need them. What’s more, those solutions tend to be expensive and hard to manage, potentially leaving you with empty pockets and big headaches.
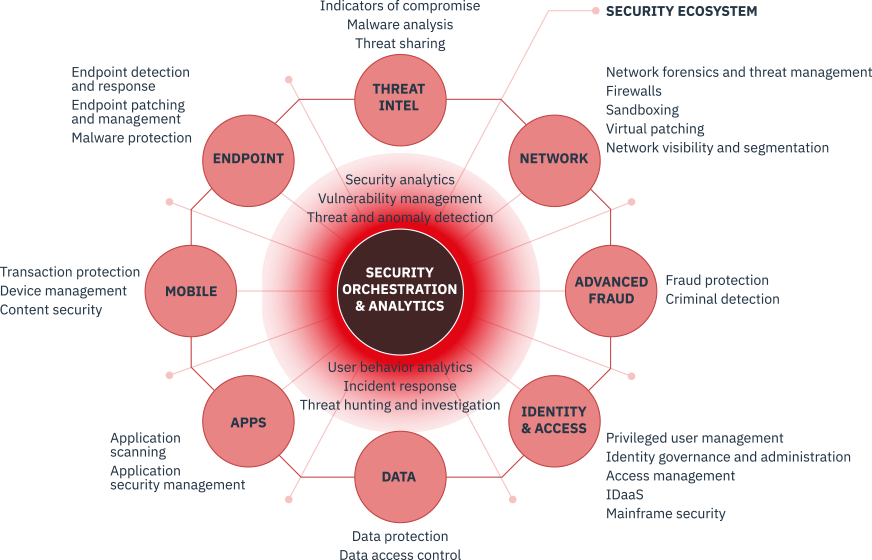
The Ssquad Security immune system is centered around a cognitive core of security orchestration and analytics which understands, reasons and learns the many risk variables across the entire ecosystem of connected capabilities.
Today, most organizations depend on web-based software and systems to run their business processes, conduct transactions with suppliers and deliver sophisticated services to customers. Unfortunately, in the race to stay one step ahead of the competition, many organizations invest little to no effort in ensuring that those applications are secure. Web-based systems can compromise the overall security of organizations by introducing vulnerabilities that hackers can use to gain access to confidential company information or customer data.
The first Cloud Cyber Security Platform which:
Cybersecurity vulnerabilities and critical issues regarding business assets like:
| Web APP SCAN | Network SCAN | Code Review |
|---|---|---|
Security testing and security scan of web applications to identify vulnerabilities |
This feature scans networks and devices, identifies vulnerabilities and helps fixing them |
Code review provides an accurate analysis of the source code in order to identify vulnerabilities |
Analysis of third parties applications vulnerabilities that could generate the loss or undesired access to customers data |
Network Security testing scan |
It tests source code vulnerabilities |
Compliance to OWASP model and to current laws |
It constantly verifies the compliance to current laws |
Identification of inefficiency & deficiencies |
Reporting Automatic generation of PDF and CSV reports |
It monitors internal procedures and company’s policies |
Identification of critical areas |